Special Report
Identity-First Security Maximizes Cybersecurity Effectiveness
The Future of Cybersecurity is Beyond the Perimeter
Legacy perimeter-based security is no longer enough. The rise of cloud computing, remote workforces, and interconnected devices have created a decentralized IT landscape where the old “castle wall” approach leaves critical gaps.
As digital transformation shifts and erodes the value of legacy perimeter-based security strategies, Gartner®️ notes the increasing need for an identity-first security strategy.
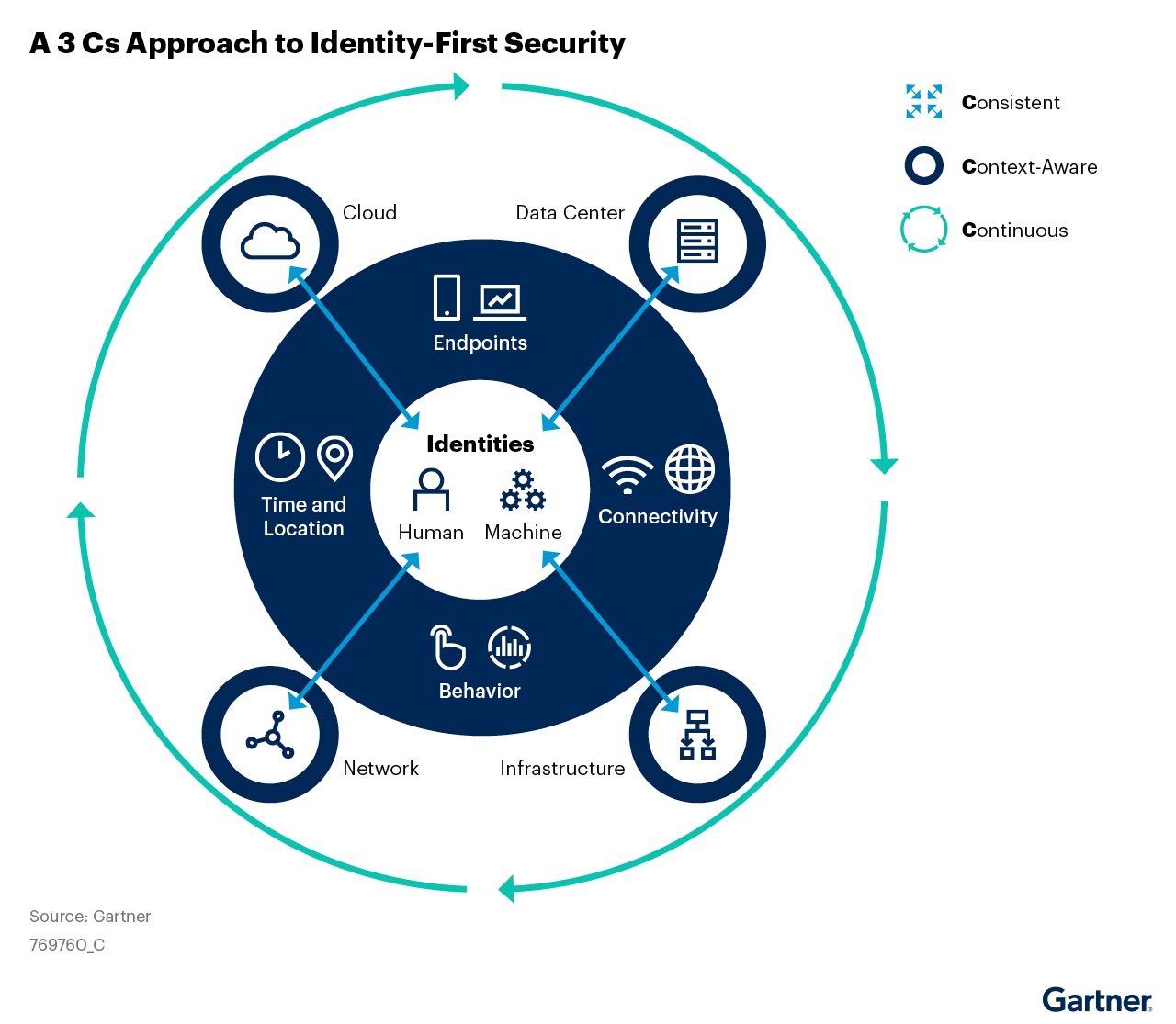
According to Gartner, to deliver identity-first security, focus on the following three C’s:
- Consistent: Use centralized policies to control access across decentralized (see Note 1), distributed digital assets in a consistent manner.
- Context: Use contextual data associated with identities and assets to drive dynamic decisions. Identify what context can be sourced and from where, and make the context available for access controls.
- Continuous: Apply adaptive controls throughout the session, not just at login.
Gartner, Identity-First Security Maximizes Cybersecurity Effectiveness, 7 December 2022, Rebecca Archambault Et Al.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Read the full report
first, we just need a few details
Additional exclusive resources
Trusted by leading companies








