Video
Detect and manage risky access with AI
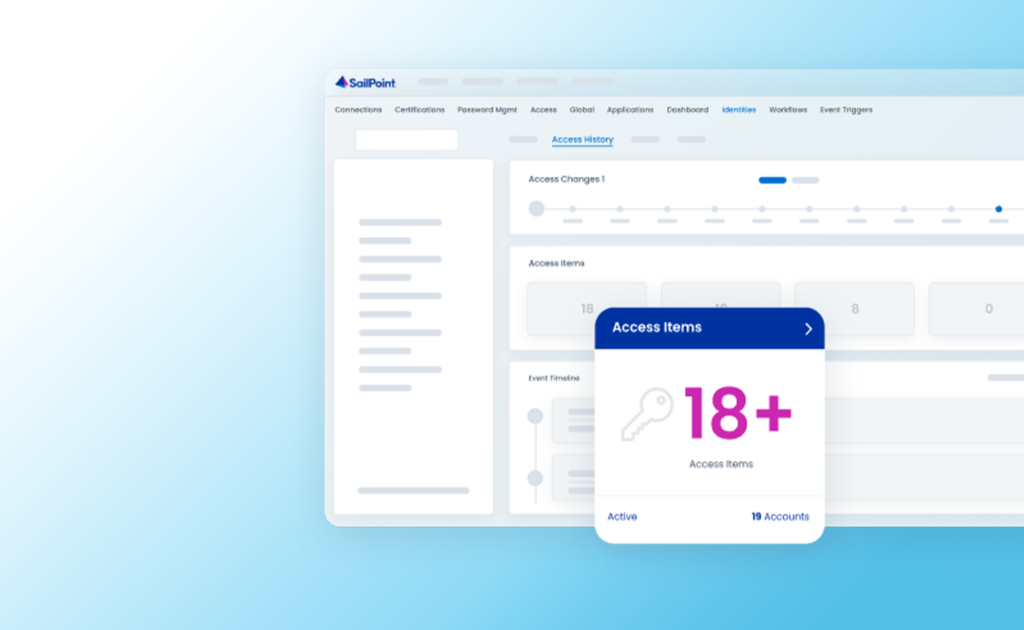
The traditional identity governance programs rely on annual certification campaigns which only look at access after-the-fact. Application owners and people managers end up manually approving hundreds, maybe even thousands of application access changes without any information that helps them make the decision. The more access that you provide to people who don’t need it the more exposed you leave the organization.
What if your identity security solution could detect access for an identity that is vastly different from its peers and provide real time information detailing why the anomaly was flagged as potentially risky? In addition, automated workflows are available to guide you to make the right access decision with the click of a few buttons. You have the proof you need to either keep, revoke or investigate the access further, based on the risk parameters you’ve set for your organization.
Join our experts to learn about Identity Outliers, the risk they pose to your organization, and the importance of managing anomalous access to ensure your access model stays current and aligned to your business needs.
Watch the video
First, we just need a few details
Additional exclusive resources
Trusted by leading companies