Overview
Neutralize threats with advanced security
SailPoint is committed to maintaining the confidentiality, integrity, and availability of our products and the data belonging to our customers, partners, and platform.
Program
Cybersecurity Program Management
Program Governance
In accordance with ISO 27001 and SOC 2, SailPoint has established an Information Security Management System (ISMS) as the basis of its corporate security program. The ISMS takes a top-down approach to security with support and commitment starting with the Executive Leadership Team and cascading down throughout the Enterprise.
Additionally, SailPoint builds a strong foundation for its Cybersecurity Program through effective policies, standards and procedures supplying business partners with the information they need to operate in a secure and compliant environment while assuring the Enterprise is taking the required and desired approach to Cybersecurity, results are as expected and benefits enable the business to create or promote value. Cybersecurity Policy provides a foundation for the implementation of Cybersecurity Strategy and the process and rules under which a secure program is offered, managed and governed for the Enterprise.
Cybersecurity Awareness and Training
SailPoint intentionally builds and fosters a cybersecurity aware workforce to promote and embed expected security behavior in all who have access to information and systems. As such, a Cybersecurity Awareness and Training program is managed and maintained requiring regular completion of security education and awareness modules, including phishing susceptibility tests. Additionally, SailPoint includes training for role-specific skills required to protect information and systems effectively and enable individuals to fulfill their cybersecurity responsibilities.
Risk Management
SailPoint’s environment is continually assessed for risks, threats and vulnerabilities associated with the loss of confidentiality, integrity, and availability. Risks are classified and prioritized according to a consistent set of well-defined criteria enabling assessments to deliver consistent and comparable results. Remediation and treatment plans are developed and a responsible party is assigned along with target timeframes for completion.
Vendor Security Risk Management
SailPoint maintains policies and procedures assuring all new suppliers, SaaS applications, IT Software and IT service solutions are subject to reasonable due diligence and validate their ability to meet enterprise security and compliance requirements as well as business objectives. This includes regular review to confirm the supplier continues to maintain appropriate compliance and security postures.
Architecture
Cybersecurity Architecture and Engineering
At SailPoint there’s nothing we take more seriously than cybersecurity. Our architecture function ensures that we leverage best in class security vendors and that our security architecture designs are in line with best practices through rigorous requirements analysis, design testing, design approvals, and robust engineering support to deploy, tune, and maintain optimized security control posture. Assuring mission success and in turn, your security, we invest heavily in enterprise security and the architecture driving it.
Data Security
SailPoint has implemented and maintains technical and organizational measures to deliver an appropriate level of data security, including policies, standards and procedures directing the controls for common concerns such as data segregation, data encryption, data handling and classification and data loss protection.
For more information on how SailPoint implements security controls to protect data and maintain strong corporate security hygiene please visit the below link:
- SailPoint Data Security Program (see Privacy for more on Data Privacy)
Cloud Security
SailPoint’s Cloud approach supports secure design, build and evolution of the enterprise cloud architectures. SailPoint’s Cloud operational and security controls are aligned with industry benchmarks and best practices such as the Center of Internet Security Community Defense Model v2.0 (CIS CDM v2.0) for setting priority on Safeguards and CIS Benchmarks.
Network Security
SailPoint implements industry leading technologies and controls to protect network security, including firewalls, intrusion prevention systems, monitoring, network segmentation, VPN and wireless security. Networks are purposefully designed and configured to restrict connections between trusted and untrusted networks. Network security architecture, designs and controls are regularly monitored and reviewed.
Operations
Cybersecurity Operations
SailPoint’s cybersecurity operations center team continuously detects and responds in their effort to tirelessly protect and monitor SailPoint for malicious activity and vulnerabilities across SailPoint environments.
Threat Detection and Response
SailPoint uses industry-standard measures to detect and remediate malware, viruses, ransomware, spyware, and other intentionally harmful programs or tactics used in attempts to gain unauthorized access to information or systems. SailPoint monitors and analyzes information and events using next-generation detection, analytics and response tools to recognize potential security threats before they have a chance to disrupt business operations.
Threat Exposure Management
SailPoint leverages industry leading vulnerability scanning technology to manage our attack surface and reduce our exposure to threat actors who would seek to exploit vulnerabilities. SailPoint has defined intervals to conduct vulnerability scans. Identified vulnerabilities are scored using the Common Vulnerability Scoring System (CVSS) risk-scoring methodology and control analysis to inform likelihood of exploitation. Vulnerabilities are remediated in accordance with defined service level agreements (SLAs) and the basis of assessed risk.
Product
Product Security
SSDLC
SailPoint is committed to delivering solutions meeting or exceeding industry standards for security. We deliver on these commitments by adopting a robust Secure Software Development Lifecycle (SSDLC) program built upon industry best practices. Please see below for an overview of our SSDLC phases.
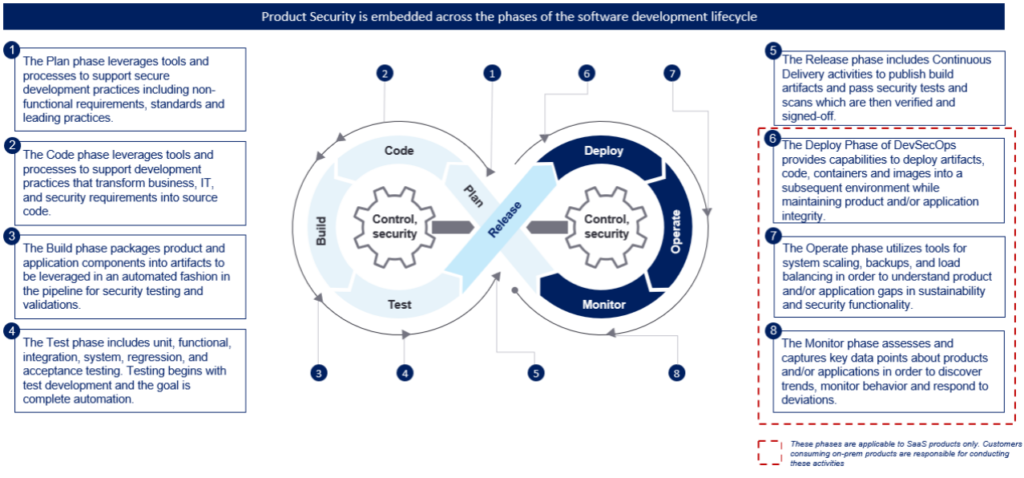
Code Assurance
SailPoint developed software is monitored and tested using SSDLC processes designed to proactively identify and remediate vulnerabilities. Additionally, first – and third-party application security assessments and penetration tests are performed at regular intervals.
Bug Bounty
SailPoint also supports ongoing external security researcher engagement to discover and remediate potential security findings.
Read more about how we engage the external security research community in the SailPoint Product Security Disclosure Program.
Product Security Advisories
SailPoint publishes Security Advisories for vulnerabilities identified in SailPoint Products. The Security Advisories provide vulnerability information and mitigation/fix guidance. To view the latest Security Advisories, visit SailPoint Security Advisories.
FAQ
Frequently asked questions
Data security is complex, and knowing where to start can be a challenge when you’re investing in a product or solution. We’re here to help. Find answers to common questions below.
The customer is responsible for establishing and maintaining the security controls in its environment.
IdentityIQ utilizes AES-256 encryption for all sensitive data and passwords. Keys are generated and managed within the IdentityIQ application and are stored in a local, password-protected key-store. IdentityIQ can also leverage a third-party tool for encryption. In addition, data masking can be accomplished for attributes classified by the customer. IdentityIQ supports encryption over the wire when reading and writing data from/to managed systems exploiting available encryption technologies such as TLS and SSH when connecting to directories, systems, and databases. IdentityIQ provides encryption via TLS for many other systems while data is in transit.
In the web layer, IdentityIQ uses JavaServer Faces (JSF) which is an industry standard, official Java API for rendering web application pages. JSF makes sure that all aspects of the component rendering are appropriately escaped to prevent instruction of scripting vulnerabilities. For the portions of the product where JavaScript toolkits and AJAX are used to improve the usability and scalability of the product, all input is passed through cross-site scripting checks to make sure that the data is not returned to the browser in a way that will cause it to be executed.
In the persistence layer, IdentityIQ uses the industry standard Hibernate package. SQL injection is prevented through the use of parameterized prepared statements in Hibernate. IdentityIQ has a few instances where direct SQL is used through Hibernate’s Query Language (HQL) and in these cases automated test suites are used to inspect and catch any issues that might be introduced.
IdentityIQ is certified for Common Criteria ISO/IEC 15408 conformance, specifically the Common Criteria IT Security Evaluation Enterprise Security Management Identity and Credential Management Protection Profile. Common Criteria Certification provides independent, objective validation of the reliability, quality, and trustworthiness of IT products. Common Criteria Certification is a rigorous process that includes product testing by a third-party laboratory that has been accredited by the National Voluntary Laboratory Accreditation Program (NVLAP) to perform evaluation of products against security requirements. Common Criteria Certification is a requirement for software used by the US government on national security systems. The international scope of Common Criteria, currently adopted by 31 countries, allows users from other countries to purchase IT products with the same level of confidence, due to the recognition of the certification across the 31 complying nations. More information on Common Criteria Certification is available at https://www.commoncriteriaportal.org/, and the IdentityIQ certification documents are available at https://www.niap-ccevs.org/Product/Compliant.cfm?PID=11043.
SailPoint is ISO 27001 certified, and the certificate is available at https://docs.sailpoint.com/wp-content/uploads/SailPoint-ISO-27001-Certificate.pdf. Information on security measures used to protect information on SailPoint systems can be provided on request.
The IdentityNow service encrypts data in transit and at rest. SailPoint’s exclusive “Zero Knowledge Encryption” encrypts credentials at the user’s device and then transmits these credentials over a communications channel adding an extra layer of encryption. Once the credentials are received by the server, they are encrypted again before being stored. No key is known or stored that would allow the credentials stored in the password vault to be decrypted. In addition, IdentityNow supports strong authentication options in order to access administrative functions, including two factor authentication methods and integration with a number of third-party authentication solutions.
For a description of the technical and organizational security measures employed by SailPoint, please see SailPoint’s SaaS Data Security Program at https://www.sailpoint.com/legal/customer-agreements/.
IdentityNow is ISO 27001 certified, and the certificate is available at https://docs.sailpoint.com/wp-content/uploads/SailPoint-ISO-27001-Certificate.pdf. SailPoint completes a SOC 1 Type 2 and SOC 2 Type 2 audit of the IdentityNow service annually. The SOC 3 report for IdentityNow is available at https://docs.sailpoint.com/wp-content/uploads/SailPoint-IdentityNow-SOC-3-Report.pdf.
IdentityNow is hosted on Amazon Web Services (AWS) cloud platform, which provides substantial protection for the base infrastructure, including the virtual servers, data storage, databases, network, and other resources. AWS follows a rigorous approach to security and maintains compliance with ISO 9001, ISO 27001, HIPAA, PCI, SOC, CSA, FedRAMP, FERPA, and other compliance programs. Please see https://aws.amazon.com/compliance/programs/ for additional information.
SailPoint maintains a Security Incident Response Plan, which specifies the steps, roles, and responsibilities should a security incident occur. This policy addresses remediation and follow-through to ensure the issue is understood and fully addressed. SailPoint will notify the customer of any security incident that involves customer data.
The customer is responsible for its IdentityIQ environment, including security breach management.
