Vendor risk management is a framework used to identify, assess, mitigate, manage, and monitor risks associated with business partners. These include:
- Consultants
- Contractors
- Retailers
- Manufacturers
- Software as a Service (SaaS) providers
- Service providers
- Suppliers
- Wholesalers
The scale of this threat makes vendor risk management a critical part of organizations’ security programs. Vendor risk management aims to ensure that internal security protocols are extended to outsiders with access to sensitive information and resources. It is applicable to many business areas, including:
- Business continuity
- Compliance
- Cybersecurity
- Financial
- Geographical
- Information security
- Legal
- Operational
- Reputational
- Strategic
- Transactional
In addition to allaying concerns about information security and data privacy, vendor risk management helps ensure compliance with laws and regulations. Among the laws that hold organizations responsible for making sure that vendors meet compliance requirements are:
- California Consumer Privacy Act
- Children’s Online Privacy Protection Act (COPPA)
- European Union’s General Data Protection Regulation (GDPR)
- Gramm-Leach-Bliley Act (GLBA)
- Health Insurance Portability and Accountability Act (HIPAA)
- US Privacy Act of 1974

Non-employee risk management increases operational efficiency by providing full visibility into third-party identity access while ensuring the organization meets regulatory compliance requirements.
With vendor risk management, organizations have a structured approach to gaining and maintaining visibility into who they work with, how they work with them, and what security controls are in place. For instance, it includes evaluating whether data privacy functions and security controls are adequate.
Importance of vendor risk management
With every step organizations take to close security loopholes, cybercriminals find others. Vendor risk management goes a long way towards closing a commonly exploited security gap.
Vendors that organizations work with often do not have a security infrastructure and processes that are on par with those of the hiring company. Cybercriminals take advantage of these weaknesses and use them as a way to gain access to enterprise systems.
Vendor risk management is important because it provides a framework for identifying and mitigating threats that would otherwise go undetected.
The impact of vendors’ vulnerabilities can be reduced to decrease an organization’s risk exposure. Organizations that create and implement vendor risk management programs not only uplevel security, but also streamline overall operations.
Benefits of VRM
A vendor risk management framework provides many benefits to organizations, including helping organizations:
- Address changing business requirements
- Adhere to defined security standards for protecting customer data
- Aggregate all vendor-related information in a centralized, accessible location
- Avoid unexpected costs or liabilities
- Enforce contract terms
- Enable compliance with evolving laws and standards
- Evaluate security measures and identify risk reduction opportunities
- Facilitate budget and cost control
- Maintain consistent vendor guidelines and processes
- Meet regulatory expectations and satisfy auditors’ expectations
- Minimize the effects of the disruption to a supply chain
- Optimize vendor due diligence processes
- Partner with the right vendors
- Protect the organization’s reputation and relationship with clients
- Provide visibility into data streams and access
- Streamline the vendor onboarding process
- Track the status of vendor questionnaires
- Track interactions with vendors over time to evaluate vendor performance
- Understand how data flows, where it is stored, and how to manage access to it
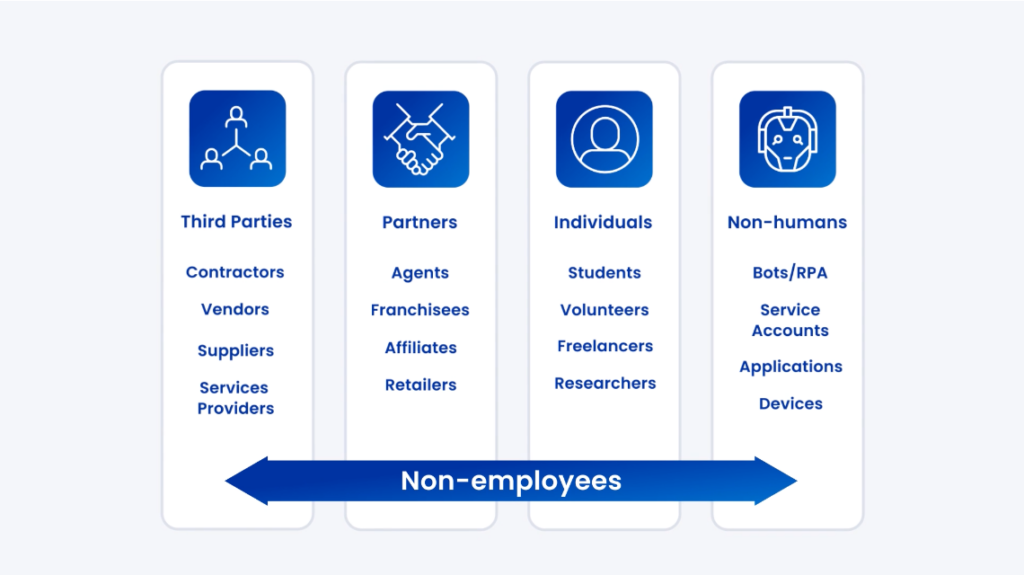
Vendors vs third parties
Vendors and third parties are often used interchangeably, but they are not the same. At a high level, all vendors are third parties, but not all third parties are vendors.
| Vendors | Third Parties |
| External entities that provide goods or services to an organization, such as: -Cleaning service providers -Cloud service providers -Manufacturers -Payment processors -Raw materials providers -Suppliers (e.g., company uniforms, office equipment, manufacturing parts, food) -Website hosting providers | Made up of vendors as well as other outside entities that the organization engages with, such as: -Accountants and auditors -Business and management consultants -Consultants and contractors -Customers -Law firms -Marketing and advertising agencies -Regulatory agencies -Students and volunteers -Venture capitalists |
Vendor lifecycle management
The vendor lifecycle is a crucial part of vendor risk management, as each point is fraught with risk. Understanding how roles and connections change throughout the phases of the lifecycle must be factored into vendor risk management programs. The vendor lifecycle, as it pertains to vendor risk management, has six phases.
Phase One: Planning
Establish processes to:
- Define the need for a new vendor
- Assess potential risks if the vendor is engaged
- Outline tasks, responsibilities, and workflows to facilitate risk assessments
- Develop a standard for how onboarding will be managed
- Maintain a vendor inventory that includes vendors’ classification based on risk tiers:
- High risk, high criticality
- High risk, medium criticality
- High risk, low criticality
- Medium risk, high criticality
- Medium risk, medium criticality
- Medium risk, low criticality
- Low risk, high criticality
- Low risk, medium criticality
- Low risk, low criticality
- Facilitate vendor communication
- Streamline the ongoing monitoring of vendor relationships
- Create documentation for choosing future vendors, collecting vendor details, and establishing ongoing reporting processes
Phase Two: Vendor selection
Research and evaluate vendors’ risk profiles by:
- Asking questions related to data protection practices
- Obtaining certifications and attestations of compliance
- Understanding the types and frequency of security training conducted internally to mitigate risk
- Determining how often vendors perform internal risk assessments
Phase Three: Contract negotiation
Once a vendor has been selected, the contract phase begins, which includes drafting a contract that details:
- Terms of the agreement
- Expectations
- Responsibilities of each party (e.g., service level agreements or SLAs)
- Reporting structure and processes
- Data governance requirements
- Plan to mitigate any risks identified in the vendor selection process
- Disaster recovery planning
- Audit processes
Phase Four: Vendor onboarding
Key parts of the onboarding process include:
- Getting vendors onboarded with the organization’s networks and systems they will need to use
- Gathering information to create a robust vendor profile
- Integrating the vendor into the organization’s workflows
- Defining and implementing access controls based on what data the vendor needs
Phase Five: Continuous monitoring
When a vendor risk management program is launched, systems need to be in place to collect data that can be used to ensure that vendors are meeting requirements for performance, compliance, and security. Based on this data, adjustments and refinements should be made to optimize the program.
Phase Six: Vendor offboarding
The final, but very important phase in the vendor management lifecycle is vendor offboarding. This process should ensure that data shared between the two parties is preserved or disposed of properly and review the contract to ensure that all obligations have been met.
Vendor risk management maturity
A vendor risk management maturity model is used to evaluate the maturity of an organization’s third-party risk management program against a comprehensive set of best practices. The maturity assessment includes an evaluation of the organization’s cybersecurity, IT infrastructure, data security, and cyber resiliency.
Key components of a vendor risk management maturity model are:
- Program governance
- Policies, standards, and procedures
- Contracts
- Vendor risk identification and analysis
- Skills and expertise
- Communication and information sharing
- Tools, measurements, and analysis
- Continuous monitoring and reviewing
Organizations use a vendor risk management maturity model to establish a baseline for building an initial program and setting goals for subsequent phases. Using a maturity model helps organizations create the most effective program by tailoring it to meet current needs and set a path for optimization and advancement.
A vendor risk management maturity model has five levels:
- Startup
No established vendor risk management practices are in place. - Getting started
Ad hoc vendor risk management activities are conducted, and there is consideration for a vendor risk management program. - Defined and established
A robust vendor risk management program has been planned and authorized, and activities are regularly executed, but the program has not been fully implemented and lacks enforcement and success metrics. - Implemented
A vendor risk management program is fully operational and has systems in place to collect and analyze metrics. - Revision and refinement
Once a vendor risk management program has been fully implemented, metrics are used to identify areas for improvement and optimization to deliver optimal risk reduction results.
Vendor risk management assessments
Vendor risk management assessments should evaluate common types of vendor risks and include additional risk factors unique to the organization or industry.
Compliance risk
Also known as regulatory risk, compliance risk comes into play when an organization does not meet requirements set forth by laws, industry practices, or regulations (e.g., GDPR, PCI DSS (Payment Card Industry Data Security Standard), HIPAA).
Cybersecurity risk
Any gaps in a vendor’s security infrastructure or processes can put organizations at risk of cyber attacks that can trigger related risks.
Financial risk
Financial risk can result from losses incurred due to a cyber attack or when a vendor experiences financial difficulties that disrupt product or service delivery.
Operational risk
Failure to have a solid business continuity plan in place can result in operational risk, where the delivery of services or products can be interrupted and negatively impact the organization’s operations.
Reputational risk
An organization faces reputational risk when an incident results in damage that shakes the public’s impression of the organization.
Creating a VRM checklist
Effective vendor risk management programs leverage checklists to evaluate performance and identify weaknesses. A vendor risk management checklist directs information that should be collected and managed, including:
- List of active vendors
- Onboarding and offboarding processes
- Vendor risk assessments
- Performance requirements for each vendor
- Processes to ensure vendors are assessed and held accountable
- Response plan if high-risk findings are identified in risk assessments
- Risk types each vendor poses and what risk tier they are in
- Systems for continuous monitoring
- Vendor lifecycle management process
- Vendor management policies
- Vendor risk management roles and responsibilities
Developing a vendor risk management strategy
Vendor risk management strategies will vary by organization and the risk types in the ecosystem. However, most strategies include several core functions and components, which are outlined below.
Vendor inventory
- Create a catalog of vendors the organization works with
- Document vendors according to their organizational structure (e.g., parent company, subsidiary, sub-subsidiary)
- Note details about contacts, such as the people and business units that own the relationships
- Understand vendors’ risk factors
- Prioritize vendors by the threat each pose
Activity tracking
The following should be documented and tracked:
- Products and services that vendors have been contracted to deliver
- Business processes that vendors’ products and services support
- Terms of the contracts, agreements, and other engagement details
Performance monitoring
Systems and processes need to be in place to document and track:
- Expectations and commitments for vendors’ products and services
- Methods and metrics related to measuring performance
- Consequences for underperforming products or services, or failing to perform according to expectations
Risk assessment and management
- Enumerate specific risks, such as customer data breaches, regulatory compliance violations, customer or shareholder litigation, or financial losses
- Develop a standardized approach to assessing vendor risk
- Optimize the time to risk identification and resolution
Vendor due diligence questionnaire
A vendor risk management questionnaire helps organizations evaluate new partners, assess their security posture, and identify potential weaknesses. Most organizations use a standardized vendor risk management questionnaire that covers key areas such as:
- Cybersecurity risks
- Do you collect, store, or transmit personally identifiable information (PII)?
- Do you monitor all devices connected to systems, software, and networks?
- Do you have any industry standard certifications?
- Technical controls
- Do you use a firewall?
- Do you install anti-malware and anti-ransomware on all devices?
- Do you install security patches for systems, networks, and software?
- Process controls
- Do you continuously monitor your controls to prevent cyber attacks?
- Do you have an incident response plan?
- Do you have a process to remediate new risks?
Ongoing vendor monitoring
- Review the vendor’s financial statements
- Conduct vendor audits
- Periodically request and evaluate vendors’ service organization controls (SOC) reports, business continuity plans, disaster recovery plans, and security documentation
- Assess compliance
How to evaluate vendor risk management effectiveness
To measure the efficacy of a vendor risk management program, a baseline must be established. Key metrics that are commonly used to help evaluate vendor risk management performance include:
- Cost of vendor risk management
- Identified risks and their stages within the risk remediation workflow
- Risk history—with the organization and other relationships
- Status of all vendor risk assessments
- Status of vendor contracts—active, close to expiration, expired
- Time spent on the vendor risk management program (e.g., onboarding, reviews, monitoring, compliance checks)
- Time to detect risk
- Time to mitigate risk
- Vendors in key risk categories (e.g., operational, compliance and legal, reputational, financial, cybersecurity, strategic)
VRM best practices
Commonly cited best practices that ensure the success of a vendor risk management program include:
- Categorize vendors and define their risks (e.g., operational, compliance, reputational)
- Communicate with senior management about the vendor risk management program
- Conduct a thorough review of a vendor’s risk management practices before signing a contract
- Continuously maintain and update the vendor list
- Create a complete vendor list, taking time to cross-check it against a list from accounts payable
- Educate employees and vendors with consistent compliance and security training
- Ensure that the vendor contract specifies the agreed-upon security standards and obligations
- Establish policies for staying aware of regulatory updates and ensuring ongoing compliance
- Remember to monitor fourth-party vendors
- Require vendors to complete a security questionnaire
Automating vendor risk management
Automating vendor risk management relieves a heavy burden on organizations. Solutions that automate vendor risk management are usually web-based applications. These solutions enable organizations to manage all aspects of vendor risk management from a central location with automation that streamlines key processes and tasks, such as:
- Vendor records management
- Contract management
- Vendor risk assessments
- Vendor access tracking
- Continuous risk monitoring
- Reporting
- Workflow integration
Important areas of vendor risk management improved with automation include the following.
Assess vendor risk, including regularly reviewing:
- Dark web findings
- Infrastructure and network security
- Security ratings
- Threat intelligence data
- Web application security
Facilitate questionnaire management with:
- Questionnaire status tracking and reporting
- Hosted repository for completed questionnaires
- Questionnaire validation
Automated vendor risk management provides numerous benefits, including:
- Assessing vendor risk
Facilitates collecting and analyzing information about vendor security posture, financial stability, and business practices - Enhancing visibility
Consolidates all relevant information into a software application that provides a unified view of all data (e.g., contract, compliance, security, risks, threats) - Expediting key tasks, such as:
- Continuous monitoring
- Vendor access tracking
- Vendor reviews
- Facilitating collaboration
Grants teams access to common systems, which makes it easier to share information - Improving accuracy
Reduces reliance on error-prone manual processes - Increasing efficiency
Reduces the time and resources needed to gather, store, and analyze data - Monitoring risk
Allows organizations to monitor vendors and identify potential risks in real time - Simplifying reporting
Creates a range of ready reports that provide insights into the vendor risk landscape and help track risk and risk mitigation activities as well as compliance status - Streamlining contract management
Provides a centralized repository for storing and managing vendors’ contracts and service-level agreements
Challenges and limitations related to vendor risk management solutions
Vendor risk management is critical to enterprise security. However, it is difficult to meet the nuanced security requirements of non-employees, which include vendors, with vendor risk management solutions. Among the challenges and limitations of vendor management systems are the following.
- Based on the assumption of a single contract or management point for third-party vendors and ill-suited to store data about individuals and their sometimes changing relationship with the organization (e.g., changing roles or reporting structure)
- Designed for the management of contingent workforce and third-party vendors and is not able to act as an effective system of record for the multiple populations in the ecosystem (e.g., independent contractors and student interns)
- Rely on defined workflows to coordinate sourcing, procurement, and payment with limited capabilities for configuring workflows without heavy customization
- Risk is evaluated at the vendor level rather than taking individuals into account
Gaining vendor benefit management with vendor risk management
Strong vendor risk management should be a priority for the enterprise. Regardless of size, organizations can be targeted by cybercriminals. A vendor risk management program helps the enterprise thwart threats by closing external loopholes that could provide an opportunity for unauthorized access to sensitive information and systems.
Vendor risk management provides the framework, systems, and processes to help any organization reap the benefits provided by outside resources without compromising security. Organizations that track key performance indicators (KPIs) and key risk indicators (KRIs) validate the value of a vendor risk management program.
You might also be interested in:
Unleash the power of unified identity security.
Centralized control. Enterprise scale.


